Networks Unlimited’s blog will no longer be hosted on WordPress. Please follow us on http://www.itsaboutaction.com/blog/ for tech updates, computer how-to’s and relevant business IT news.
3 Proven Methods to Prevent Costly Data Loss
17 05 2013Odds are, your business has or will experience data loss at some point. Whether it’s an accidentally deleted file or a complete storage failure on your server, the ramifications can be devastating. Assume your company lost all of its data today, and ask yourself, what data do I have backed up? Where is it? And how long will it take to restore that data and resume regular business operations? If you are unsure or uneasy about any of your own answers even in the slightest, you need to employee a better backup system. Here are 3 key proven and effective elements of a data backup plan:
Backing up your data using multiple technologies is best practice. A strategy which uses both online and offline backups provides you with flexibility from both a restore-time and budget standpoint. A well-developed backup strategy feeds directly into a disaster recovery and business continuity plan for your company. With diverse system, your data recovery is very near 100% effective.
Natural and man-made disasters can wipe out entire data-storing facilities. Geographical diversity in your strategy ensures that your data is available for restore regardless of natural disasters, network outages, terrorist attacks or communication disruptions. A combination of local on-site backups with multiple offsite locations generally guarantees that you will have a path to recovery regardless of the interruptions you can’t control. As remote facilities are generally out of your control, be sure to understand the data security levels and where your data is stored.
All too often businesses find that backup procedures were not followed properly, test restores were not performed or perhaps, the external drive you backup to, actually filled up three months ago and you have not performed a successful backup since that time. An automated and managed solution makes perfect sense for organizations whose business focus is not technology and whom do not have a dedicated IT staff. The amount of data you create and the importance of the data will determine how often you conduct your backups.
Some data loss statistics:
–60% of companies that lose their data will shut down within 6 months of a disaster
–More than one billion people have been affected by data loss incidents in the last five years.
The causes of data loss:
The good news is that data is loss is completely preventable when a backup plan is in place and utilized correctly. If you have questions about creating a back up plan, give us a call!
Comments : Leave a Comment »
Categories : Uncategorized
Partner Spotlight: GJ Company produces innovative components for biking enthusiasts worldwide
9 05 2013 
Mountain Racing Products is a partner of Networks Unlimited. As a Managed Services customer of ours, we oversee this growing company’s IT needs. We will begin to feature a new partner each month that have made great accomplishments as individuals and as a business. Mountain Racing Products produces popular parts for bicycles such as Trek, Giant, Salsa, and more. This is the story of Mountain Racing Products:
Tim Fry was sitting in a bar in a high-rise building enjoying his vacation with his wife Christy when he received a call from his law firm. A client wanted to speak with him and was not happy that he was not in his office. As a complex litigation lawyer, a lot was asked of Fry, but getting to his office while on vacation was something he simply could not do. In this moment, he realized that he needed a change. After 6 years of working on extremely challenging and complex litigation cases, Fry started to seek a new path. “As a lawyer, I was tearing things down; I wanted to build something up.”
He and his wife, also a lawyer, began searching for businesses that fit a certain criteria. They wanted to find a business that involved manufacturing, had products that were proprietary, and that had export potential. In 2000, he purchased a biking parts business in Grand Junction, CO.
 Coming from Ohio, he had only ever skied in Colorado and was not familiar with Grand Junction. Certainly, Colorado had appeal, but it wasn’t until after two years in Grand Junction that he and his wife knew that they were here to stay. Over dinner one evening, Christy told him, “You realize we’re not leaving, right?” Fry said he knew then that he had to make it work.
Coming from Ohio, he had only ever skied in Colorado and was not familiar with Grand Junction. Certainly, Colorado had appeal, but it wasn’t until after two years in Grand Junction that he and his wife knew that they were here to stay. Over dinner one evening, Christy told him, “You realize we’re not leaving, right?” Fry said he knew then that he had to make it work.
Fast forward to 2013 and Mountain Racing Products is found in over 35 countries around the globe. Professional bike-riders and enthusiasts around the world have parts from pedals to chain guards to suspension on their bicycles made right here in Grand Junction. Fry says that it is exciting to visit other parts of the world and see his product on shelves and in use. They have found a lot of success in niche products and Fry told us about a time he saw a police officer riding a bike with his pedals in an airport. The pedals, Power Grips, are a product that has become increasingly popular with law enforcement because the grips secure a shoe but are comfortable enough to attach to normal footwear. In an airport in Columbus, Fry spotted his pedals on a police officer’s bike and caught up with the office for a photo-op.
Mountain Racing Product’s “Power Grips” pedals are very popular with law enforcement cycles because they comfortably fit normal footwear.
Mountain Racing Products are well-known and very popular in the biking industry with their brands White Brothers, Kreitler Rollers, Tamer, and Power Grips. Though Western Colorado is a Mountain Biking Mecca, Fry says, “We have to remember that only about 3% of our total sales are done in Colorado.” With supplying to a global market, the Mountain Racing Products team must always consider, implement and develop new products that appeal to riders of all types of terrain and conditions.
As much as 40% of the company’s products are made right here in the Grand Junction. The remaining products are created where their business partners’, such as Trek, Giant and Salsa Cycles, manufacturing facilities are located. These huge biking brands have parts made from Mountain Racing Products directly on their bikes such as Salsa Cycles’s Horsetheif 2 bicycle (pictured below) . Mountain Racing Products also makes specialty parts for Trek, Giant, and others, when needed.
Fry and his wife jokingly refer to themselves as “recovering lawyers.” They are very happy with the business they have built but admit that owning and operating their own business consumes far more time than being lawyers. Fry laughs and adds that people in the biking industry are generally happy and are definitely happier than the people he dealt with in his previous profession.
Recently, Mountain Racing Products was awarded as one of “Colorado’s Companies To Watch.” To receive this award, companies must be privately held in Colorado, experiencing growth, have 6 to 99 full-time employees and have $750,000 to $50 million in sales. We congratulate

Sheets of metal are turned into the bicycle parts such as this at the facility in Grand Junction

Salsa Cycles, has Mountain Racing Products’ White Brothers Suspension stock on their HorseThief 2 model
Comments : Leave a Comment »
Categories : Partner Spotlight
Tens of Thousands of New Malware Programs Created Each Day
3 05 2013 Some reports from say that there are 35,000 new malware programs created each day, while other studies report 70,000 new malware programs each day. Now, McAfee is reporting 100,000 new malware programs are created on a daily basis. Though these figures are estimations and vary with results, we can gather that there are A LOT of malware being created each day.
Some reports from say that there are 35,000 new malware programs created each day, while other studies report 70,000 new malware programs each day. Now, McAfee is reporting 100,000 new malware programs are created on a daily basis. Though these figures are estimations and vary with results, we can gather that there are A LOT of malware being created each day.
In most cases, malware is created to gather sensitive information. With the information gathered, identities can be stolen, banking info collected, credit card numbers taken, internet history recorded and more. Other malware can be more a nuisance and not cause true harm to your system other than slowing it. Regardless of the intent of the malware, avoiding getting a virus or other malware is crucial.
Antivirus, knowing what to look for, and knowing how to strengthen your computer security is key to prevent an infection on your computer. There are still risks of infection even after taking precautions, but antivirus software providers work diligently around the clock to update their databases and systems to best protect your computer. Though infection is still likely with antivirus, using such programs are a proactive measure to preventing catastrophic data loss.
This infographic from Kaspersky outlines the consequences of cyber attacks for both businesses and personal computers:
You can learn about how to protect yourself more from some of our previous posts:
Current Common Computer viruses
How to Create Strong Passwords
There are many effective and affordable options for antivirus software and programs. We will gladly answer any questions regarding programs for you.
Comments : Leave a Comment »
Tags: computer, computer virus, malware, virus
Categories : Computer Security, Virus Protection and Security
Welcoming New Team Member, Gibran
29 04 2013 Gibran is the newest engineer to join our team. With his addition, we have grown to nineteen employees at Networks Unlimited; preserving our title as the largest IT provider in Western Colorado.
Gibran is the newest engineer to join our team. With his addition, we have grown to nineteen employees at Networks Unlimited; preserving our title as the largest IT provider in Western Colorado.
Gibran has grown up in various parts of the valley and lived in Palisade, Grand Junction, and Fruita. He first became interested in IT after visiting his family in California who work in the technology industry.
For the past five years, Gibran has worked and gained professional experience in information technology in Grand Junction. We are excited to have him continue his career in IT with Networks Unlimited. When asked what his favorite part of working in IT is he says, “I like that every day is different.”
For the past two weeks, Gibran has accompanied our other engineers on jobs as he learns the ropes at Networks Unlimited but is excited to now be working independently. His first job on his own will be at the Colorado National Monument. We know that he will demonstrate the quality work and professionalism that we are known for.
Please help us welcome our newest team member!
Comments : Leave a Comment »
Tags: colorado IT company, grand junction it, IT, Networks Unlimited
Categories : Networks Unlimited Updates
Renting a Computer Server: An Alternative to Purchasing.
26 04 2013Servers can be a costly, but necessary, expense for businesses. As businesses find themselves in the position of shopping for a new server, there is another option: Server as a Service.
We have outlined the major differences between Server as a Service (renting a server) and purchasing a server.
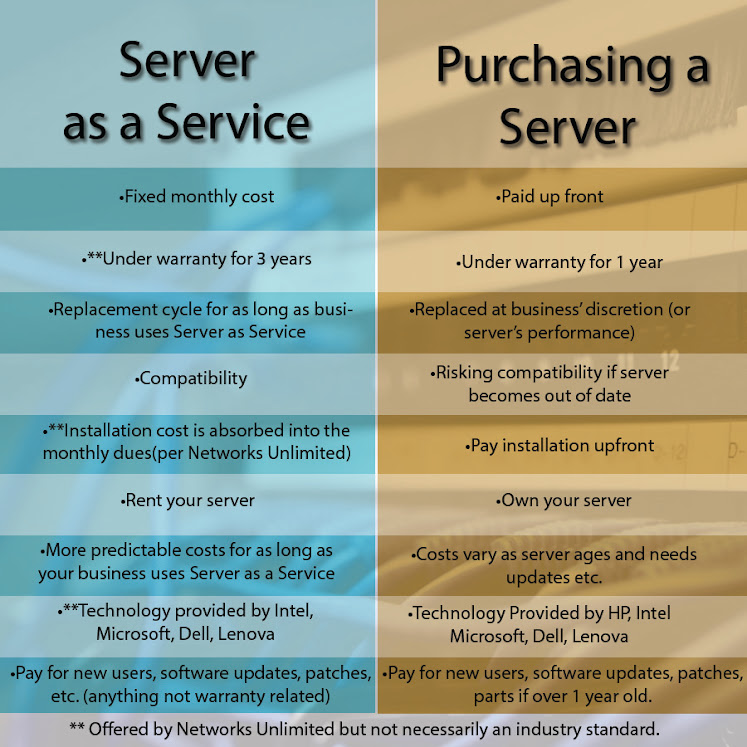
If you would like to know about Server as Service as offered by Networks Unlimited, call us or comment!
Comments : 2 Comments »
Tags: new server, renting server, SaaS, server, server as a service, server rental, servers
Categories : Business IT, IT, Networks Unlimited Updates
Your small business can write off more tech spending in 2013
19 04 2013Can your small business thrive if you are depending on outdated technology? Probably not. You need current technology today to communicate with your clients and customers, examine sales trends and more successfully handle everything from bookkeeping to payroll. Fortunately, the American Taxpayer Relief Act of 2012 includes a hefty tax break for small businesses that put money into new technology. Here’s a brief look from BizTech Magazine at how this tax break works and how it can help your small business stay on top of the technology curve.
An important tax break
According to the American Taxpayer Relief Act, businesses can now write off as much as a rather notable $500,000 of new technology and equipment expenditures in 2013. This may provide small businesses with the boost they need to more vigorously update their technology. Businesses, for instance, might elect to upgrade their computer operating systems to Windows 8. Or…
View original post 174 more words
Comments : Leave a Comment »
Categories : Business IT
Free, Simple & Quick Computer Security Update for Windows
19 04 2013Updating your security is a proactive way to ensure that your computer is up and running when you need it. Even if you have anti-virus programs, it is important to keep your computer security up to date through Microsoft. Your setting may be configured to allow for automatic updating, if they are not, here is a free and simple way to make sure that your computer is up to date against the latest security threats.
What are Windows Security Updates?
Security updates are fixes to possible security threats in Windows programming and help improve the performance and reliability of windows and other applications
Why do I need to update my security?
People who create viruses and other malware look for weak and vulnerable spots in programs, Windows’ engineers work to continually update their programs to patch those weak and vulnerable parts of your system.
How often are security updates available?
Along with all other Windows Updates, Windows Security Updates are available once a week. They typically are available Tuesday afternoons.
There are also security and critical updates that can be released daily.
How does it work?
The security updates are downloaded onto your computer and any security problems are patched up.
How to update your security:
You can either do this manually or automatically and either way, it is very simple:

2. Find “Windows Update”

3. Choose “Check for Updates”
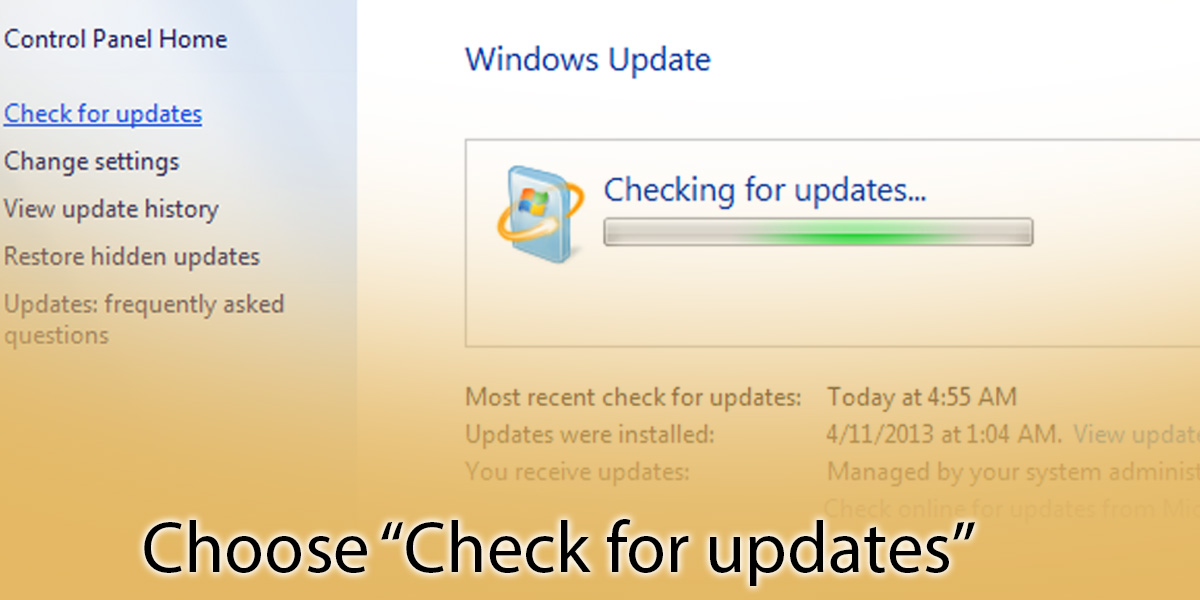
4. Your computer will either be updated or you will be given the option to update your computer. If it is updated, you will see a message like this:
(If you see this message your setting are most likely set to be automatically updated)
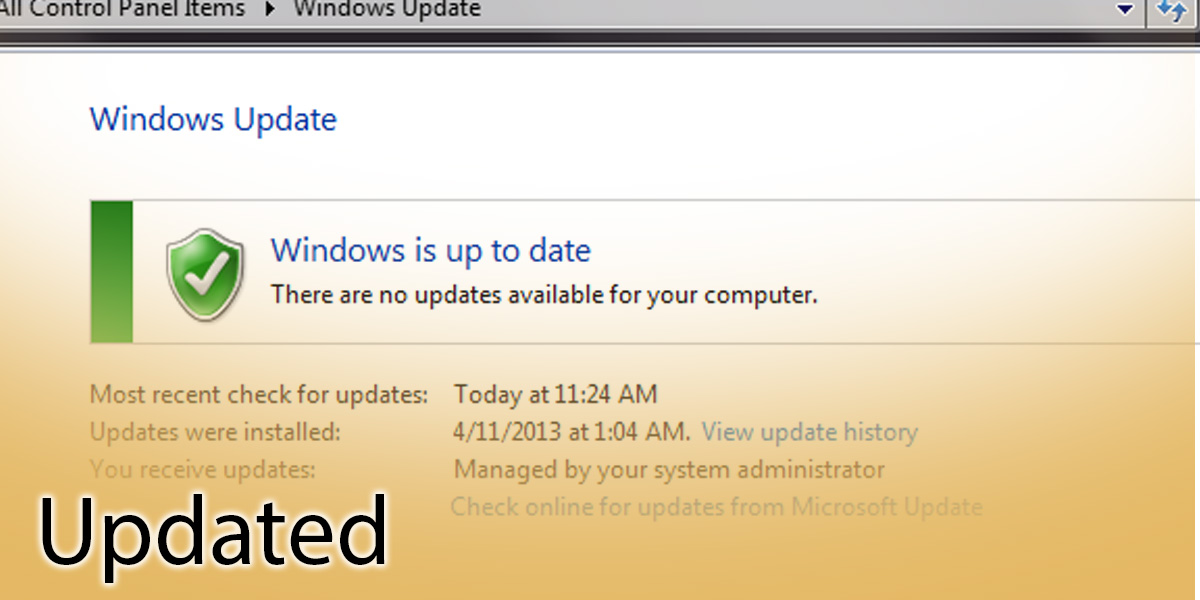
If you do not receive this message, then Windows will prompt you to update your system, which includes your security updates.
If your updates are not already automatic, changing your setting to make updates occur automatically is simple:
From the Windows Update menu, go to “Change settings” and from here, you can configure automatic updates.

If you do not want your updates to occur automatically, then go to “Let me choose my settings” and configure your settings how you prefer.
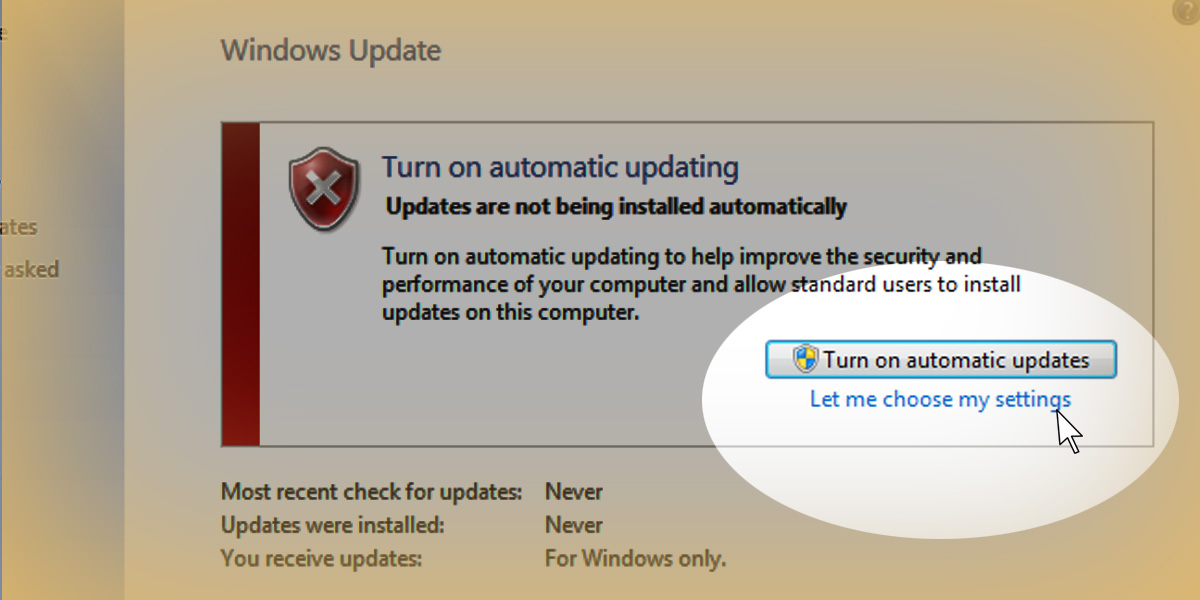
From here, you are given a variety of options to update your settings:

If you have a system administrator, such as Networks Unlimited, then chances are these updates are handled for you. If your setting are pre-set, your screen will appear like this:
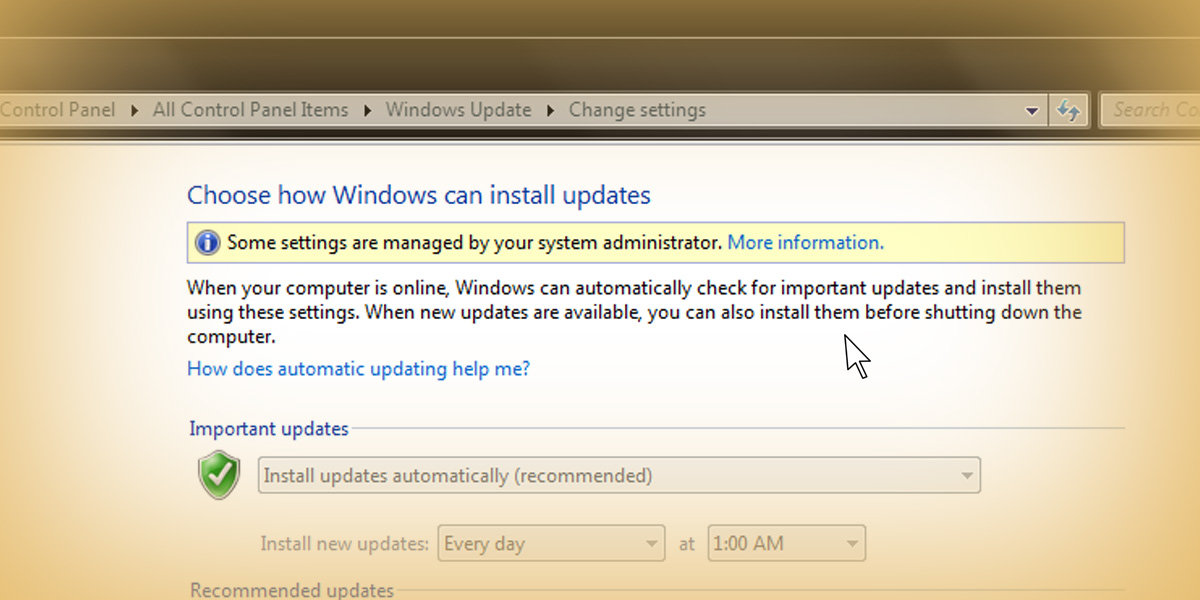
These screen shots are from a Windows 7 machine. If you have a different machine and need help, just ask . I can also provide Windows 8 screen shots- just ask!
Comments : 1 Comment »
Tags: anti virus, businesss IT, computer, computer trick, easy computer fix, how to update security, IT, microsoft, microsoft security, security update, tech, technology, windows, windows security
Categories : Business IT, How To's, IT, IT Quick Tip, Microsoft, tech
Colorado Woman Shares Experience With Mobile Phone Virus
10 04 2013KKCO 11 news spoke with Networks Unlimited about how to prevent mobile viruses and how they are becoming a growing target for hackers and malware. Our own Chris Riggs and Lauren Bell spoke about the growing problem. See the news story here.
Colorado woman, Rebecca McClelland tells her account with a mobile virus:
“A number with a 876 area code continued to call me and one time I answered. When I answered the phone the male on the other end had a foreign accent. I told him to please stop calling my phone and he continued to say I called him. I hung the phone up and they continued to call and I did not answer. Throughout the day my phone was acting funny and I was not receiving phone calls or text
messages. Around 3pm my phone was shut off and I could not make any outgoing calls.When I called my provider they said there was a fraud on my account and my service had been shut off. Needless to say I was not happy, the criminal had cloned my phone
and phone number and used all of my minutes and made international calls. My provider is able to reimburse me but they continue to call.”
Rebecca McClelland, of Grand Junction Colorado, shares her experince with smartphone hacking.
Comments : Leave a Comment »
Tags: bluetooth, mobile anti virus, mobile security, mobile virus, phone hack, phone hacking, smartphone virus, virus removal
Categories : IT, News, tech